HashStorm 🌪️: Python Tool for Hash Identification and Cracking
Jun 14, 2025 5-10 min read Project-documentation
Developed by Krishna Dwivedi
Objective
The Goal of this project is to develope a tool that can:
- Accept hash inputs from command-line (single or in batch) or from a hash file
- Identify the type of cryptographic hash from input values
- Crack those hash(es) values using:
- Dictionary-based attack
- By performing Lookup in Cracked hashes
- Brute-force attack using specified charset
- Perform a google search if hash not cracked
- Automate identification & cracking in single command
Project Description
HashStorm is a command-line utility built with Python, designed to identify and crack a wide variety of hash types. It automates the identification process using regular expression patterns from the hashid library and supports cracking through dictionary-based attacks.
The tool is specially valuable in:
- Pentest env
- CTF Competitions
- Cyber Forensics
- Password auditing
NOTE: This tool is intended only for educational purposes, ethical hacking, or penetration testing and ethical use only.
Features ✨
- Utilizes the hashid Python library to identify over 220 hash types accurately, including MD5, SHA-1, SHA-256, and others, using regular expressions for pattern matching.
- Automatically identifies hash types for one or more hash values.
- Cracks hashes using wordlists or brute-force methods (with planned updates for advanced features).
- Supports batch processing of multiple hashes from files or command-line arguments.
- Includes output saving to history, lookup file for faster cracking, and specified file, and options for future enhancements like Google searches.
- Cross-platform compatibility, as it is written in Python.
Tech Stack ⚙️
TECHNOLOGY PURPOSE
Python3.13 Core Programming language
hashid (Lib) Hash types identification
sys (Lib) CLI argument parsing
File I/O For reading writing files
Regex (Lib) For checking validity of a hash string
Hashing Libs For hashing words to crack hash(es)
Multiprocessing (Lib) For concurrent processing (default disabled due to process creation overhead)
Installation 📩
To install HashStorm, follow these steps:
- Ensure you have Python latest version installed, as the script relies on Python's standard libraries. Download Python from the official website if needed.
- Clone the repository
git clone https://github.com/SudoHopeX/HashStorm.git - Move to the HashStorm directory
cd HashStorm - Install python modules(libraries)
pip3 install -r lib_requirements.txt[ In kali-linux direct pip3 installation is not permitted without virtual environment upto my current info, so if an error arises use venv ]
- You are good to go, to use 'HashStorm'
Usages
Run
python3 hashstorm.py --help //to display below given usage information.The default icrack mode simplifies workflows by handling both identification and cracking automatically
USAGES:
python(3) hashstorm.py [Options] [Arguments]
OPTIONS:
> --help print tool usages
> identify identify the hash-type of specified hash-value
> crack crack the hash-value (!NOTE: hash-type must be passed)
> icrack [Default] automatically identify hash-type and crack the hash-value specified
ARGUMENTS:
> -h <hash-value(s)> Add one or more hash-value to crack or identify followed by ','
> -hf <hashes file> Pass a hash file
> -H <hash-type(s)> Pass hash-type to crack
> -w <wordlist-path> Specify wordlist to use for cracking hash
> -o <output-file> Save result in specified file
> -v Verbose mode ( show detailed info while cracking ) [in update]
> -g Perform a google search if hash not cracked [in update]
> -brute Crack hashes using self defined charset and length [in update]
> -charset <charset> Specify character set for bruteforccing like "a-z,0-9" [in update]
> -length <pass-max-length> Specify hash word's maximum value [in update]
EXAMPLES:
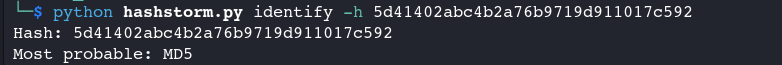
> python hashstorm.py identify -h 5d41402abc4b2a76b9719d911017c592
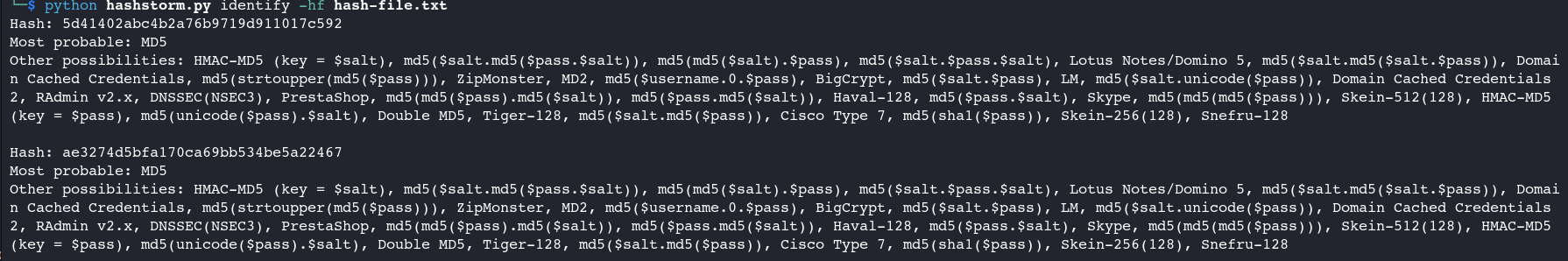
> python hashstorm.py identify -hf hash-file.txt
> python hashstorm.py identify -h ae3274d5bfa170ca69bb534be5a22467,5d41402abc4b2a76b9719d911017c592
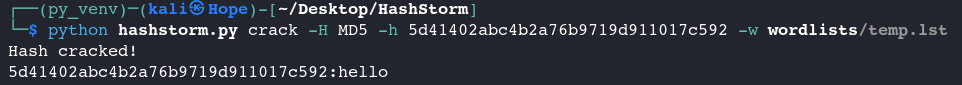
> python hashstorm.py crack -H MD5 -h 5d41402abc4b2a76b9719d911017c592 -w wordlist.txt -o output.txt
> python hashstorm.py crack -H MD5,MD5 -h 5d41402abc4b2a76b9719d911017c592,5d41402abc4b2a76b9719d911017c592 -w wordlist.txt
> python hashstorm.py -h 5d41402abc4b2a76b9719d911017c592 -w wordlist.txt -o output.txt
NOTE:
> Tool usages format must be followed
> Atleast 'hash-value' OR 'hashes-file' must be passed as argument
Demo 🪧
Identify a single hash 👇
Identify from file 👇
Crack a known MD5 hash using wordlist 👇
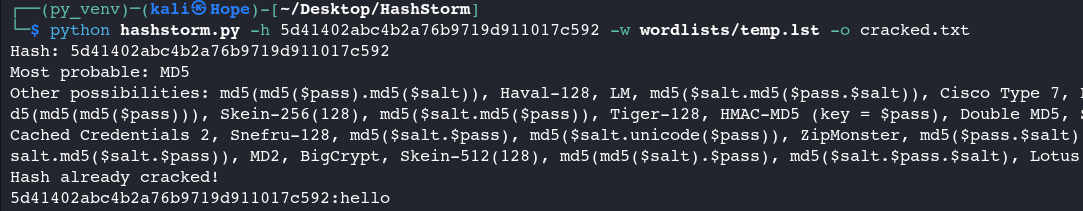
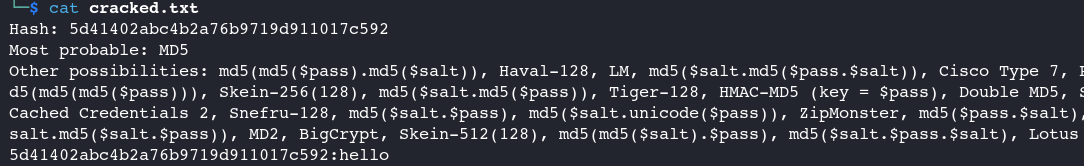
Use default icrack Mode (identification & cracking automation) & save result to a file 👇
Planned Improvements
- Brute-force engine with charset + length
- Advanced google query integration for finding uncracked lookups
- GUI mode
- Hashcat integration
Contributing
Contributions to HashStorm are encouraged to improve features, fix bugs, or add support for more hash types. To contribute:
- Fork the repository on GitHub.
- Create a new branch for your changes.
- Submit a pull request with a detailed description of the changes.
- Before contributing, test your modifications thoroughly.
License 🪪
This project is licensed under MIT. See LICENSE file for more info.
Acknowledgments 🙏
- Inspired by hashid tool in kali for hash identification
- Thanks to resources like HashID module in python for hash identification techniques.
